Simplify APIs and trusted services communication
Bridge the gap between devices and services through secure, automated exchanges. Whether it's IoT or background processes, ensure the integrity of data.
Forge trustworthy bridges for both internal and external APIs
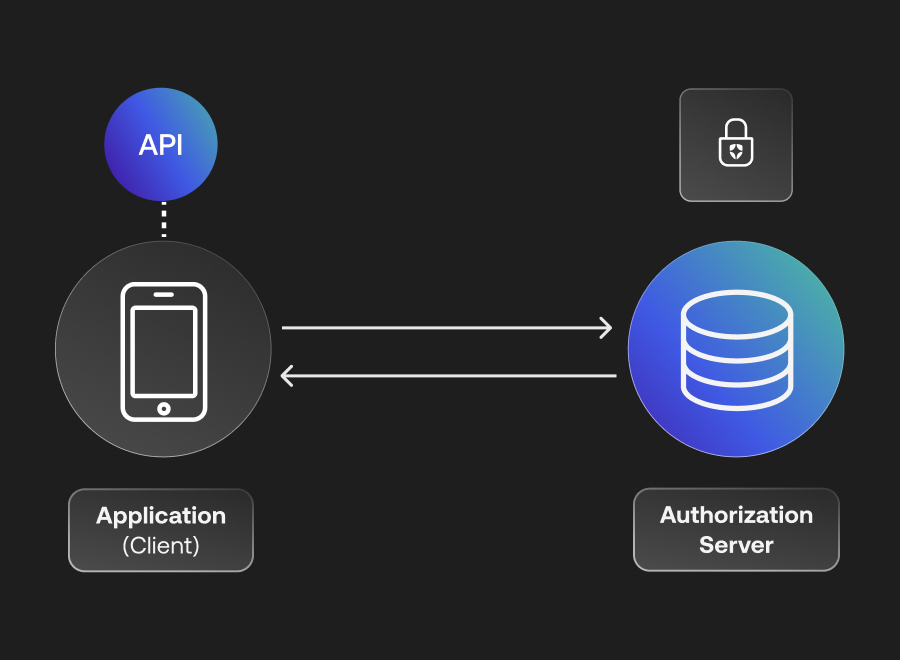
Empower your APIs to communicate securely with non-interactive third-party applications. Keep it simple:
• Applications authenticate themselves to Auth0 via their Client Id and Client Secret.
• Auth0 verifies the information and responds with an Access Token.
• Armed with the Access Token, applications can confidently call the API.
Go beyond human identities with IoT
When machines talk, make sure it's secure. Leverage the unique Identity of each IoT device for a streamlined, impenetrable communication setup.

Seamless API onboarding for non-interactive apps
Integrate non-interactive applications like servers, CLIs, daemons, and more into your ecosystem. They might operate in the background, but their security takes the front seat.
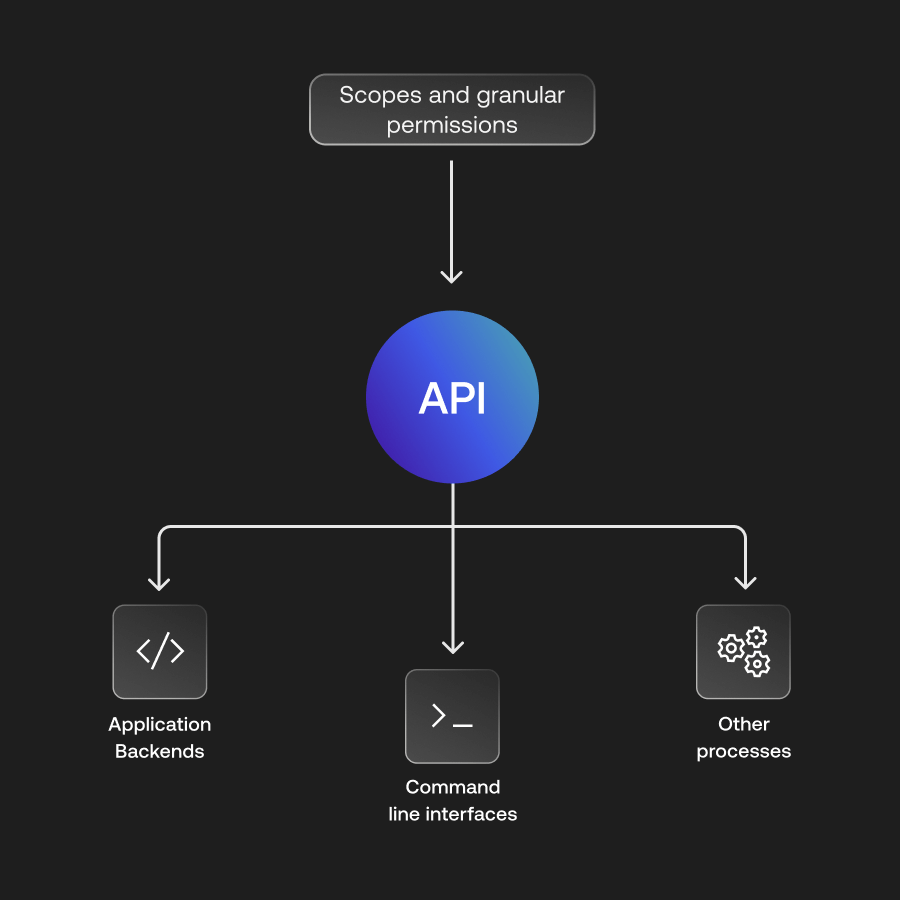
Scopes and granular permissions
Chart the course for every client's journey in your API landscape. Grant or restrict access based on granular permissions:
• Application Backends
• Command line interfaces
• Miscellaneous processes
Application Backends
Let application backends, APIs, and services join the conversation without any human nudging.
Command Line Interfaces
Craft robust CLI tools that seamlessly plug into and communicate with your APIs.
Continuous Processes
Empower job schedulers, daemons, and consistent system processes to guard and engage with your API.
Security backed by standards
Sleep better knowing every byte of data exchanged adheres to globally accepted standards. Dive into the OAuth2 Client Credentials Grant flow, and witness security in motion.

Ready to dive in?
Unlock the potential of seamless machine-to-machine communications.